7 Ways to Boost Cybersecurity This 2024

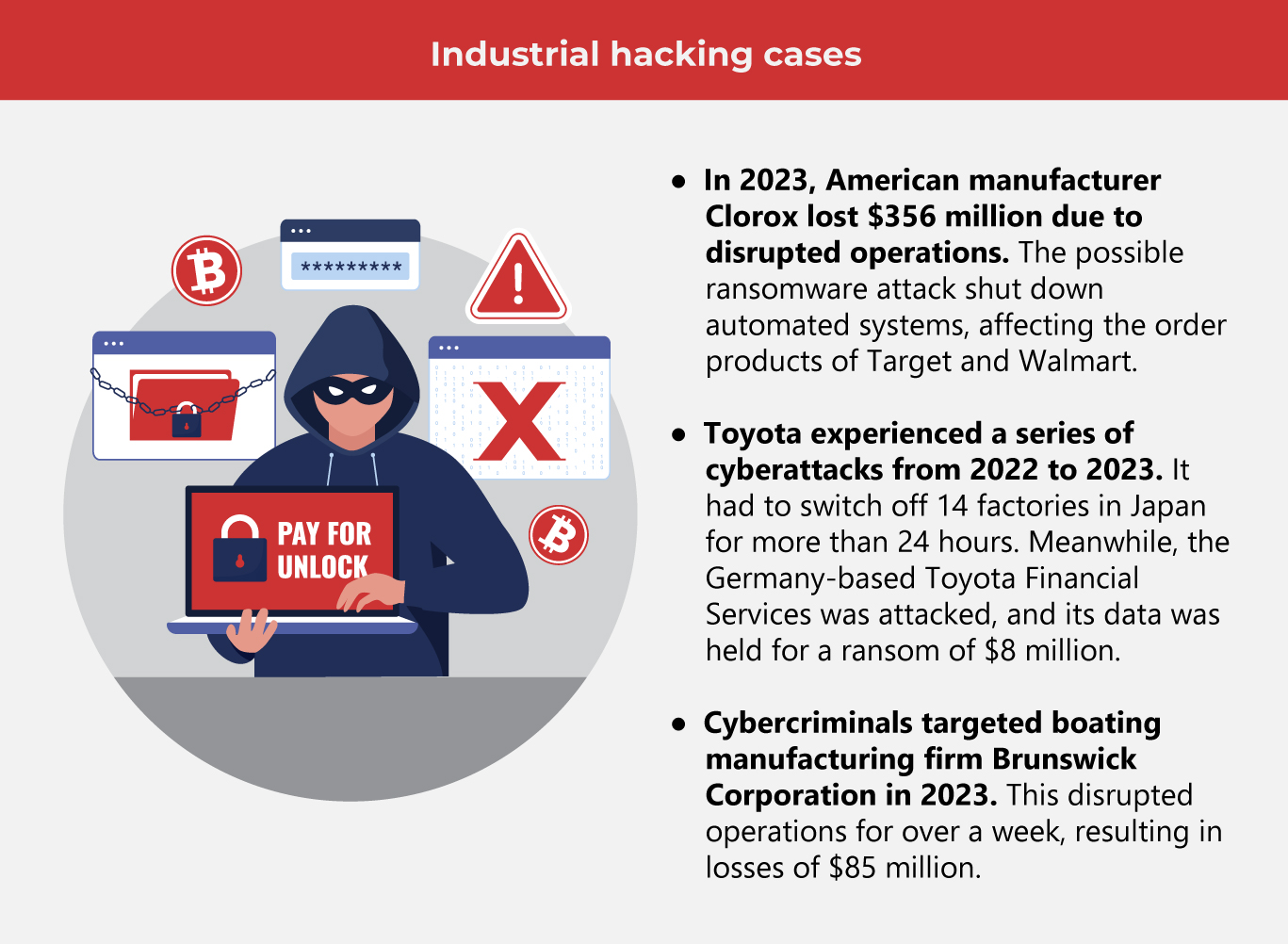
The manufacturing sector is the target of growing cyberattacks, which disrupt production lines and threaten labor-saving operations. According to a study, ransomware attacks against industrial companies rose by 50% in 2023. Manufacturing organizations were the target, experiencing 70% of the attacks.
Cybersecurity, which is the buzzword in business protection, refers to an organization's capacity to sustain its essential operations, not only when under attack but also during recovery. Connected to this is cyber threat intelligence (CTI), which means collecting, analyzing, and spreading information about threats to an organization's digital resources.
A vital part of digital asset management, CTI produces actionable insights by predicting and reducing the likelihood of cyber threats. With this skill, businesses can formulate defensive measures even before attacks, improving their response and decision-making.
Global manufacturing organizations need to learn about CTI, especially considering the variety of threats cybercriminals utilize. From classic strategies like phishing to more modern attacks that are challenging to stop, online threats are plentiful and relentless. It takes only one small oversight for them to succeed, leading to widespread business disruption.
Why cybercriminals are targeting manufacturing companies
The manufacturing industry is one of the leaders of technological innovation. But this progress comes with the price of attracting the attention of cybercriminals, out to derail production lines and steal valuable information. Here are some reasons why manufacturing companies are the main target of cyberattacks:
-
Automation as a risk
The intricate and interconnected nature of today's software and hardware supply chains makes manufacturers appealing targets for hackers. Because this sector depends on an interconnected technology network, cybercriminals can access several companies with just one successful attack. The abundance of susceptible endpoints across various environments increases the likelihood of infiltration.
-
Potentially huge pay-out
Imagine a whole factory halting operations because of hacking. This potentially results in order delays, product shortages, and financial losses. With this also comes reputational damage as clients and partners lose confidence in the organization's ability to consistently deliver. According to this report, more and more manufacturing firms are willing to shell out higher ransoms. This drives cybercriminals to focus on this sector as pay-outs can be high.
-
Security gaps
Innovations in artificial intelligence (AI) and machine learning (ML) are excellent for streamlining operations. However, security lapses in these areas can enable cybercriminals to automate precision-targeted attacks, leading to widespread breaches. This is why companies need to assign a team to monitor operational technology. Before the digital revolution, engineers who knew little about information technology (IT) took over this responsibility. But with digitalization thrown into the mix, employees must now be equipped with CTI to increase cyber resilience.
7 ways to boost cyber threat intelligence
Cyber threats have become inevitable, making CTI an invaluable strategy for protecting digital assets. Here are some ways to address your system's vulnerabilities and prepare for an online breach.
-
Study your system's interconnectivity.
Evaluate your internet-linked assets and study their relationships. Knowing how they work together lets you identify the potential consequences of a breach. To protect your asset data, link it across systems within a network, including subnetworks and distributed environments. This way, you improve asset visibility, monitoring, and anomaly detection. To make monitoring faster and easier, you can automate corrective functions like sending alerts, installing software, executing remote commands, refreshing security scans, and managing user account permissions.
-
Make security testing a priority.
Top management support is crucial when prioritizing cybersecurity measures. Though having a competent cybersecurity team is important, it's just as vital for company leaders to advocate and participate in data security initiatives. Leaders should recognize that this aspect is not a separate IT task but an issue that affects the whole organization. Cybersecurity should be a regular topic in boardroom meetings while companies train their employees on CTI and invest in security testing tools.
-
Comply with risk management standards.
In the EU, the NIS2 or the updated version of the Network Information Systems directive, requires specific organizations to implement various information security controls. This currently most extensive European cybersecurity directive introduces more stringent standards for managing risks and reporting incidents. It also covers more sectors and imposes harsher penalties for non-compliance. Meanwhile, the US has the NIST Cybersecurity Framework to mitigate and manage cybersecurity threats. To learn more about cyberattack techniques, visit MITRE, which offers a free knowledge base built on real-life observations.
-
Draft an action plan.
To ensure preparedness, try simulating a cyberattack in your specific manufacturing environment. This lets you spot areas where fast decisions should be made. For instance, which personnel is assigned to particular machines? Who makes the final decision for the factory shutdown? The response depends on the scale of the attack and your operations, so it's best to formulate a plan as early as possible so you don't have to fumble for solutions.
-
Physical security matters.
With all this talk about cybersecurity, it's still important to consider physical security within and around your manufacturing facility. Can anyone access the areas that hold your operational technology? Is there a way for third parties to go around security? Be vigilant against insider threats, especially when equipment suppliers can access the site remotely. The security measures they use to verify their employees are crucial and should be part of the supplier contract.
-
Monitor your employees.
Disgruntled or ill-intentioned workers may steal sensitive information, inject malware, or impair systems. Employees can also be innocent but still be victimized by malicious individuals who trick them into divulging private data through phishing and social engineering. Workers who aren't trained in cybersecurity may use weak passwords, enabling attackers to gain access. Those who don't know protective measures may inadvertently download malware, click on dubious links, or fall for scams.
-
Cultivate an environment of cyber resilience.
While technology can help you fend off cyberattacks, you should also focus on the human element when promoting a vigilant culture. Everyone in the organization has a role in ensuring cybersecurity, so consistent training and awareness initiatives are necessary. This strategy fortifies your defense against external threats and reduces risks from deliberate and unintentional insider threats.
By incorporating cutting-edge technologies, ongoing education, and thoughtful strategizing, companies can cultivate a resilient culture that tackles present-day threats while able to confront unforeseen challenges in the future. As one of the Top 20 EMS companies in the world, IMI has over 40 years of experience in providing electronics manufacturing and technology solutions.
As one of the Top 20 EMS companies in the world, IMI has over 40 years of experience in providing electronics manufacturing and technology solutions.
We are ready to support your business on a global scale.
Our proven technical expertise, worldwide reach, and vast experience in high-growth and emerging markets make us the ideal global manufacturing solutions partner.
Let's work together to build our future today.
Other Blog